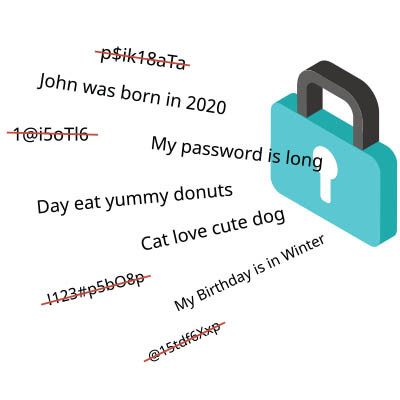
We’re doing something a little different this time around. Normally, we try to keep the focus on business technology, but this article is geared towards the typical low-tech home user.
These days, nearly all human beings are wrapped up in a little technology, and there isn’t a huge divide between protecting yourself as an employee at a company versus protecting yourself as an individual—at least as far as cybersecurity habits go. Even if you feel like you are pretty low-tech, you still have to worry about protecting your identity, financial information, and personally identifiable information online.
We encourage you to share this article around with everyone you can, from students to those enjoying their retirement. We all have family or friends who have a loose ream of paper they scrawl their passwords onto, or might even have worse habits that they think are perfectly healthy that are putting them at risk. This article might help them reduce the risk of expensive, frustrating problems.
If you were sent this article, hello! There is someone who cares about your safety online and wants to try to make your digital life a little easier. We hope you find this guide useful, and we’d love to get feedback from you if you have any!



![How to Get Your Passwords in Order, and Keep It That Way [Part 5 of 5]](https://www.directtechnologygroup.com/images/easyblog_shared/January_2025/1-15-25/b2ap3_large_Protection_602670589_400x400.jpg)
![How to Get Your Passwords in Order, and Keep It That Way [Part 4 of 5]](https://www.directtechnologygroup.com/images/easyblog_shared/January_2025/1-13-25/b2ap3_large_ProtectPassword_612796604_400x400.jpg)
![How to Get Your Passwords in Order, and Keep It That Way [Part 3 of 5]](https://www.directtechnologygroup.com/images/easyblog_shared/January_2025/1-10-25/b2ap3_large_MFA_519254719_400.jpg)
![How to Get Your Passwords in Order, and Keep It That Way [Part 2 of 5]](https://www.directtechnologygroup.com/images/easyblog_shared/January_2025/1-08-25/b2ap3_large_PasswordManager_409150837_400x400.jpg)
![How to Get Your Passwords in Order, and Keep It That Way [Part 1 of 5]](https://www.directtechnologygroup.com/images/easyblog_shared/January_2025/1-06-25/b2ap3_large_StrongPassword_530099076_400x400.jpg)