One of the handiest keyboard shortcuts of all time is probably Ctrl + F, or Find, which helps you locate specific text on a page. That said, you can also do some neat things besides finding specific text. You can also replace text, even to the case and special characters. Let’s get into how you can do so in Google Docs and Word.
Direct Technology Group Blog
Isn’t it funny how, despite there being so, so many emojis to select from, you so often can’t find one that succinctly and descriptively gets your point across? Google has recently added a feature to its Gboard mobile keyboard called Emoji Kitchen.
Emoji Kitchen does what it sounds like and cooks up blends of two emojis for you. Let’s go over how to use it.
Google's recent decision to push more remote staff back to the office, with potential consequences for non-compliance, feels like a step backward in the evolution of workplace flexibility.
While the tech giant cites the importance of in-person collaboration and a stronger company culture, this rigid stance overlooks the significant benefits and increasing acceptance of remote work, especially for small and medium-sized businesses (SMBs).
In keeping with the modern trend of incorporating artificial intelligence into everything we do, Google has been moving full steam ahead with Gemini, the company’s latest AI model. While once available only to those willing to pay the “Advanced” plan’s $20-per-month fee, Google recently announced that many new features would be available for free… including the capability to reference a user’s Search queries and other Google applications to further personalize that user’s results.
Let’s go over how to set this up, but also, why you may want to refrain from doing so.
Another month, another batch of security updates. Google has been busy squashing 43 bugs in Android, and—surprise, surprise—two of them were zero-day vulnerabilities. That means bad actors could’ve been exploiting them before Google even knew what was up. Obviously, this isn’t good and highlights why it’s important to keep your software updated.
If you’ve ever used Google Lens on a mobile device, you know it’s a pretty impressive little tool for contextual searches. However, you can also use these capabilities in the Chrome browser., searching for anything visible in the browser—from text to images, even one captured from a video.
Let’s go over how.
You’ve probably noticed that Google searches are sometimes a little different these days. Depending on what you search for, sometimes Google will attempt to provide an AI-generated answer. A lot of Googlers have noticed that sometimes these answers get a little wacky. What’s going on? Why isn’t Google just taking users to websites like they used to? And what is the impact of all this AI stuff?
Laptops are nothing new for businesses. In fact, some recent laptops have the processing power to eclipse your typical desktop workstation. However, this doesn’t apply to all laptops, as evidenced by the Chromebook. Today, we want to explore the big differences between Chromebooks and your average laptop, as well as how you might choose between one or the other.
Are you familiar with the works of Isaac Asimov? The author wrote a short story called “Runaround” in 1942, and it introduced the idea of the Three Laws of Robotics, or laws that all of the robots in his Robots series must follow. This stranger-than-reality concept is being used today by Google, which has announced a set of safeguards partially inspired by these three laws to help it control future AI-powered machines.
AI might feel like a technology perfectly at home in the world of science fiction, but the truth is that most of its uses are not nearly as interesting or fun. Take, for example, Operation Green Light, an initiative from Google that aims to better society through examining AI for traffic control and its impact on the environment.
Have you tried using Enhanced Safe Browsing in your Google Chrome browser? This feature has been a part of the browser since 2019, and it was implemented with the intention of preventing phishing attacks. This feature was also recently added to Gmail. Here’s how you enable it, as well as why it might not be the solution you’re hoping for.
Google is one of the world’s biggest technology companies, but have you ever wondered how exactly it manages to maintain its iron grip on the search engine market? It’s especially curious when you consider that there are other major technology companies out there that might want a piece of the pie, like Apple, yet choose not to. Well, it turns out there is a very good reason for that, and as you might suspect, large amounts of money are involved.
Google is rolling out client-side encryption to Gmail and Calendar, which will allow users to create meeting events as well as send and receive emails that have been encrypted before being sent to Google servers. Client-side encryption will be available to organizations with Google Workspace Enterprise Plus, Education Standard, and Education Plus plans. All other types of Google Workspace accounts and personal Gmail accounts will not get client-side encryption.
Most people use their smartphones more than any other computing tool, and businesses must adapt to these trends if they want their employees to be as productive as possible. Businesses can capitalize on their employees’ smartphone use if they are strategic in their implementation of mobile device tools and strategies—including work profiles on Android devices.
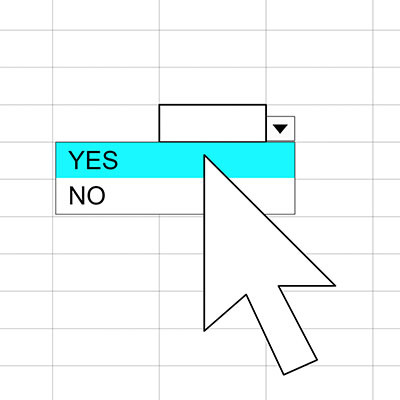
If you know how to use functions and various other features that Microsoft Excel and Google Sheets have to offer, then you can take your skills one step further than most. One such feature is the use of dropdown menus within cells. Let’s discuss how you can use them to your benefit in both Excel and Sheets.