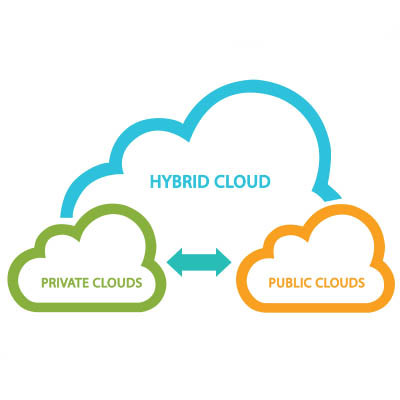
How many times have you felt like it’s impossible to keep up with today’s rapidly evolving business technology? You’re not alone; small businesses all over are finding it to be expansive and fast-moving, making it hard to stay ahead. If you’re sick of underutilizing your resources, maintaining broken systems, and overspending on your IT, then it’s time to start looking for savings.
Direct Technology Group Blog
As an IT expert who has spent years under the hood of various professional service firms, I’ve noticed a recurring pattern. Many lawyers are brilliant at practicing law but are often held back by a digital anchor; outdated servers, fragmented files, and manual billing processes that eat away at billable hours.
In 2026, staying competitive isn't just about your legal acumen; a lot of it is about your tech stack. If you want to scale your firm, protect your clients, and have a chance to reclaim your weekends, here are the four technologies your office needs to run optimally.
How often have you been frustrated by the challenges of installing new software? How about expiring licenses or outdated tools that need to be upgraded frequently to prevent them from becoming obsolete? These are all problems associated with buying software licenses, and they can all be avoided through the smart use of Software as a Service.
By “renting” access to applications with a SaaS model, you can lay the foundation for a more efficient, secure, and scalable infrastructure, all while potentially setting yourself up to punch at a higher weight class than your SMB might have been capable of in the past.
Most modern businesses are powered by their on-premise server hardware assuming that it creates a more secure environment for them. While having your data close by, where you can easily access it, sounds like a great idea, know that there are also issues that arise from these kinds of arrangements. In fact, your business might be the most dangerous place you can host your data. Here’s why.
No matter the size or industry of your business, effective communication is a constant challenge that dictates where you spend your tech budget.
Fortunately, there is a simple, strategic, and powerful solution: Voice over Internet Protocol (VoIP). This modern technology is a sound upgrade from traditional telephone systems and is ready to transform your communication infrastructure for the better.
You won’t get far on our website without finding an article or two talking a big game about the cloud and what it can do for your business. One thing is for certain: you can’t underestimate the value of securing your cloud solutions. It doesn’t matter what you use it for; cloud security is an integral part of ensuring your operations continue unimpeded and uninterrupted.
Are you running a business without a mountain of cash? You’re not alone. Every dollar matters, and tech choices can be stressful. Do you grab the cheapest tool and hope for the best? Do you even feel like you have real options? Here’s the good news: You don’t need a huge budget, you need a smart game plan.
If you're a young entrepreneur or professional trying to grow your business without burning through cash, this one's for you.
If you want to discuss the single most influential technology for the modern era, there’s a lot of competition—but the cloud is a serious contender. Through the cloud, your organization can pull off feats previously impossible for all but the largest and most profitable companies. Today, we want to look at how small businesses use the cloud and how you benefit from the various models.
For years, traditional telephone systems have been a cornerstone of office communication. However, many companies have yet to update their phone systems to match the evolving needs of the modern workplace. Today, we explore how Voice over Internet Protocol (VoIP) is revolutionizing business telephone systems.
In order to survive in today’s business world, your organization needs to be adaptable and flexible to new situations. You might have to take on the persona of a bookkeeper, HR, and other important roles for your business. You can add “IT decision maker” to that list, as 95% of small businesses in the US utilize some kind of computing to keep the business running smoothly.
The cloud has made quite a splash, even in our everyday lives. Think about it: how else would all those streaming services work, if it wasn’t for the cloud? Entertainment at our fingertips aside, we’re big fans of cloud services for business purposes, and there are a few very good reasons for that.
Six, to be specific.
When it comes to getting the most value out of your business’ software infrastructure, it’s hard to argue with Software as a Service (SaaS). In fact, there are many solutions that are fueled by SaaS that power some of the world’s most lucrative companies. Let’s look at some examples of SaaS applications that can help even a small business revolutionize operations to save time and earn more profits simultaneously.
Evolving considerations are definitely a major part of doing business. A decision made a year or even a quarter in the past might not be right for your business today. When trying to establish a technology profile that is right for your business, it can be difficult to nail down exactly what solutions allow you to improve overall efficiency while supporting organizational productivity. In today’s blog, we try to give a couple of tips for when to establish when it is time to shift gears and consider new tech.
TV shows and movies captivate people of all ages, walks of life, and socio-economic backgrounds. They can put viewers in places in time and situations that they could only dream about. Like many things in our society, there are varying roles that technology plays in the entertainment industry. Let’s take a look at the role technology plays in the creation of the entertainment that we enjoy every day.
Most businesses leverage the cloud in at least some capacity, whether cloud-based apps or cloud-based infrastructure. In any case, using the cloud comes with inherent security questions that must be addressed during the planning, implementation, and launch phases of any solution. Let’s go over some of the ways you might protect data and applications stored in the cloud.
Technology has become a fundamental need for businesses of all sizes, with even small businesses needing to seek out options to cover their shifting needs. Fortunately, this technology has also become more reliable and readily available…and as a result, small businesses have more opportunities than ever to give their operations a welcome boost.